Modern adversaries can now integrate cyber operations into military plans. Recent events have shown that rival governments can not only develop cyber-attack plans, but synch them to achieve national goals. The U.S. Department of Defense must begin integrating and normalizing the use of cyber effects. While there are numerous methods to begin that process, the key is choosing a method and beginning the long process of training in its employment. The primary level this training should be performed is at the Army Division level. Often, the division is the first major headquarters that can develop a list of requirements to submit to the Joint Task Force Headquarters or the Combatant Command. With that in mind, training at home station and during operational level exercises is absolutely necessary. Simulation technology will catch up with cyber operations in due course, but this is no reason to not begin training now.
As a military, the US faces adversaries that have proven their ability to integrate offensive cyber effects from the tactical up to the strategic level. Though multiple methods exist to request and execute Cyber Operations (CO) at the division level, the bigger and more looming problem is the lack of training in utilizing these effects, and being ready to put these effects to use on the battlefield. For the United States to keep pace with near-peer nations, it must train on and prepare to use these effects in a real-world combat environment.
What is Available to Division Planners? The U.S. Army Operating Concept states that a critical component to a strategic victory is being able to present the enemy with multiple, simultaneous dilemmas to contend with.1 Going forward, cyber options present a perfect additional capability to bring into the fight. Cyber Electromagnetic Activities (CEMA) personnel should maintain their subject matter expertise on tools that are currently in use, but also should be ready to make requests for new cyber tools. Nothing should prevent the planner from asking for a specific effect as long as it properly addresses the commander’s intent. Requirements developed through the CEMA Working Group and approved through the targeting process will drive tool development. As the requirements list moves up the chain, the next hurdle to overcome is negotiating with higher echelons on what level of command should retain execution authority. The most important portion of this process is getting requirements up to the next higher level of command.
At what level? There are a few schools of thought on what command level should conduct cyber operations. The JP 3-12 indicates that CO should be integrated at all levels, and in all military operations. However, usage of offensive cyber operations at the division level requires military units to rethink how they perceive the ‘level’ of operations.2 More to the point, one of the Major Army Warfighting Challenges directly addresses the optimal method by which to support Unified Land Operations at all echelons.3 As long as divisions are generating requirements that do not massively overstep their given mission, Army divisions can confidently say they are getting after that challenge.
This is not to say that Army units at all levels should be given carte blanche to cyberattack the adversary. It is a typical practice to limit certain activities to higher echelons. The primary reasoning behind it is to ensure those effects that have much further reaching results are controlled to avoid unnecessary collateral damage or unforeseen effects. Some weapons also should be withheld from a lower echelon because their effects can have strategic implications (i.e. nuclear munitions). It stands to reason that authority to release cyber effects should be held at a considerably higher level than a division. That being said, this should not preclude divisions from asking for tailored effects that support the ground commander’s vision.4 In fact, the division planners stand the best chance of requesting cyber effects that could substantially affect the conflict within their Area of Operation (AO).
Higher echelons do not typically direct specific tactical actions for maneuver units. It is not practical and higher echelons will not have the sort of tactical situational awareness required for effective decision making. Consequently, senior commands would most benefit by allowing divisions a substantial amount of authority to synch cyber operations as it nests with their overall execution plan.
Division planners can concentrate on specific effects that would have a localized effect in their AO. The assets to perform collateral damage estimates reside at levels higher than the division. It is important to perform due diligence to ensure planned effects do not propagate uncontrolled. Thus, division CEMA personnel craft the request for effects and begin a two-way discussion with the assigned Cyber Mission Teams (CMT) as the request matures.5 Bottom-up requests with top-down refinement provides the most efficient method of acquiring specific and effective cyber effects.
As a combat multiplier, CEMA personnel must look at their job as being inherently joint and thus must always work with the CMT to craft and synch requested effects. Planners must be completely clear when making requests on how their plans will nest with the command’s vision and endstate.6 The common thread of Mission Command (MC) provides a framework for CEMA planners to begin the request process.
Mission Command: The true bottom line of MC is enabling subordinate commanders to achieve the commander’s intent within certain limiting factors. This method allows for the greatest amount of autonomy but also permits a considerable amount of initiative based operations. Division Electronic Warfare Officers (EWO) have the primary responsibility in applying cyber solutions to key tasks to facilitate the commander’s picture of the endstate.7 Essential to that responsibility is understanding what is within the realm of possible for CO, and how best to synch that to a plan.8
High Priority Target List (HPTL): There is a challenge with providing cyber targets to the Division targeting cycle in that, often times, a valid and lucrative cyber target isn’t on the Commander’s HPTL. It might be the last thing one would think as a valid military target. Some of the best targets for cyber manipulation are targets the enemy never thinks to protect due to their perceived low military value. A HPTL is typically populated with kinetic weapon systems and enemy combat multipliers. CEMA personnel need to be aware of this and be able to fully explain the value of a target, and why it’s being actioned. Further, cyber targets don’t necessarily need to be located on the commander’s HPTL. They merely have to be a valid military target. The reason behind this is that servicing these targets will not involve the usage of limited divisional resources.9 Identifying targets of this nature requires the planners to ensure they are using tools based in doctrine.
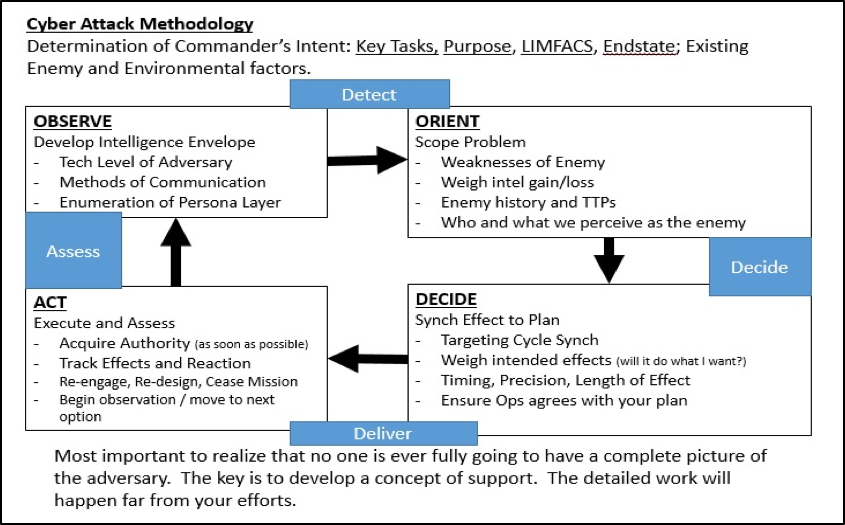
Figure 1. Example of a Cyber Targeting Cycle10
Methodology: Cyber Operations must be fully integrated into the targeting process. The process of bringing cyber effects can work the same way that typical lethal targeting works. That being said, the planning horizons of CO are considerably different.11 The level of target fidelity is often unknown to a requesting unit, and at the Division level, access to pertinent targeting data may or may not exist. It’s almost never possible to have perfect information. This type of target granularity is not an absolute requirement. The primary job of the CEMA staff at division is to develop a listing of requirements and immediately push these requests to their higher headquarters as soon as there is a decision to move forward with a cyber Course of Action (COA).
It is possible for a unit below Corps to get wrapped up in the intricacies of fine-grain cyber target development. What is most important for Division CEMA planners is to be aware of what cyber techniques are possible, and develop the planning products to issue a request to Corps and above. Of critical importance is a well thought out and detailed Concept of Operations (CONOP). Greater detail in the CONOP will allow echelons above division to apply the proper solution, and gain sound intelligence during cyber tool development. A Cyber Effect Request Format (CERF) will sometimes be called for from the Division to accompany the CONOP. While the CERF can (and certainly should) be forwarded with the CONOP, it is operative to understand that most of the information required by the CERF will not be readily available to a division. Hence the CONOP’s absolute importance in this process.
The next key step will be well crafted Measures of Effectiveness (MoE) and detailed synchronization of effects. Knowledge of programming code and tool development can help with overall formulation of a plan, but it should not be considered a prerequisite. Measurable results gets the commander accustomed to working more cyber options into the overall plan. As stated previously, there are a number of methods for selecting targets, and provided the process yields viable targets, and can be synched to the Division’s lethal targeting process, any version will work. The following step will be to craft the request and understand what type of effect will yield the best results.
Shotgun Effect versus Chess Match.12 The design of cyber effects are an important consideration when attempting to plan at the tactical and operational level. There is literally no limit to the methods that a cyber operation can use to achieve results. For the purpose of this article, the left and right limits can be depicted by the amount of pre-coordination and planning involved in putting the effect into execution.
A menu of pre-coordinated effects colloquially named “shotgun effects” refers to effects that have all been prearranged and can be executed rapidly. These effects address a very specific problem set with coordination to use these tools performed well in advance. The tactical order they operate under defines specific targets and times the effects can be utilized. They sacrifice flexibility for responsiveness. Grouped within this category are specific cyber operations that are designed and implemented with one single purpose in mind. These “silver bullet” effects are just as specific as other shotgun effects, and will likely only be used once due to the tailored nature of the tool.
On the opposite end of the spectrum, effects that have a significantly longer term execution cycle and aim at seemingly innocuous vulnerabilities work much like a “chess match”. These effects, are often less defined and work against multiple vulnerabilities. The key to success of this type of attack is its ability to operate for a longer period of time without being discovered. This kind of attack should be aimed at systems not really deemed of significant military value, and less likely to be heavily defended. Small changes over time stand less of a chance of being discovered and can produce massive cascading effects. They would be considerably harder to fix until it is far too late in the battle. These types of operations can have the capacity to preclude a major military engagement by removing the enemy’s initiative. Plans like this are (understandably) the hardest to put into play. The operation will certainly be executed at a much higher level (than division) but, as stated before, this should not prevent units from asking for these effects. To be effective in today’s fight, Cyber/EW personnel must employ both shotgun and chess match type effects. Further, CEMA planners must effectively employ these operations against enemy vulnerabilities that may not be immediately apparent.
What enemy vulnerabilities does one attack? A trouble spot for CEMA personnel is knowing just what to target and exploit. With a small amount of creative thinking, a planner can utilize the tools available to Division targeteers to plan and execute CO. Simply put, the Division’s targeting process can be fed with cyber requirements just as it is fed with lethal requirements.
Target research. As the Cyber Attack/Defend Methodology has provided, a targeting tool (PMESII crosswalk) that can be modified to suit a cyber targeting approach.13 This method will allow CEMA personnel to cage their efforts, better produce CONOPS and formulate the basis of an effective attack. This also allows other members of the staff to visualize how CEMA looks at the enemy. Cyber planners at the division level will often have little access to make specific requests. As previously stated, full target resolution is not a necessity to make the request, but elements well above the division are equipped to do the heavy lifting to resolve a target and compute collateral damage estimates.

Figure 2. PMESII examination of adversary
Way Ahead: To become better at integrating and to normalize the use of these techniques, Division CEMA elements must train in their employment. The challenge with training CO is properly replicating effects and ensuring enough of the staff has a grasp of the cyber support plan. It begins with ensuring cyber planning is included in the division’s battle rhythm and ensuring effects are briefed during combined exercises. While most of these effects cannot be replicated in an exercise, the effects can be worked into the scenario by Observer Controllers. As scenario technology improves, so will the ability to replicate special effects as a matter of course. It is incumbent on the Division CEMA staff to press for inclusion of these effects. Educating the division staff will allow leadership to continue to involve cyber operations in their menu of options when planning courses of action. These capabilities are real and can become a normal part of division operations provided we are willing to train and use them. Conflict is going continue to increase in complexity and scope. The US military must keep pace with the changing face of warfare to ensure we can contend with any threat to national security regardless of how new or emergent it is.
About the author
 LTC James Montgomery is the Cyber Electro-Magnetic Activities (CEMA) Chief for the 4th Infantry Division, Fort Carson, Colorado. In addition to previous assignments within the signals intelligence community, he has had multiple deployments as an Electronic Warfare Officer at the Brigade and Combined Joint Task Force level. He is a graduate of the Joint Electronic Warfare Theater Operations Course and the Joint Advanced Cyber Warfare Course. He holds a master’s degree in ethics and decision making from The Pennsylvania State University.
LTC James Montgomery is the Cyber Electro-Magnetic Activities (CEMA) Chief for the 4th Infantry Division, Fort Carson, Colorado. In addition to previous assignments within the signals intelligence community, he has had multiple deployments as an Electronic Warfare Officer at the Brigade and Combined Joint Task Force level. He is a graduate of the Joint Electronic Warfare Theater Operations Course and the Joint Advanced Cyber Warfare Course. He holds a master’s degree in ethics and decision making from The Pennsylvania State University.
Notes
- S Army Training and Doctrine Command, “TRADOC Pamphlet 525-3-1, The U.S. Army Operating Concept,” October 31, 2014, http://www.tradoc.army.mil/tpubs/pams/TP525-3-1.pdf (Accessed March 3, 2016).
- S. Department of Defense, “Joint Publication (JP) 3-12, Cyberspace Operations,” February 5, 2013, x. http://www.dtic.mil/doctrine/new_pubs/jp3_12R.pdf.
- Army Capabilities Integration Center, “Army Warfighting Challenges,” December 10, 2014, http://www.arcic.army.mil/Initiatives/army-warfighting-challenges.aspx. Challenge 7, Learning Demand 3.
- Department of the Army, “Field Manual (FM) 3-0, Operations,” February 27, 2008, 5-3. http://downloads.army.mil/fm3-0/FM3-0.pdf.
- IBID, 5-3.
- S. Department of Defense, “Joint Publication (JP) 3-12, Cyberspace Operations,” February 5, 2013, 1-7. http://www.dtic.mil/doctrine/new_pubs/jp3_12R.pdf.
- FM 3-38, Cyber Electromagnetic Operations, February 12, 2014, 2-2. http://armypubs.army.mil/doctrine/DR_pubs/dr_a/pdf/fm3_38.pdf.
- Army Doctrine Reference Publication (ADRP) 6-0 Mission Command, March 28, 2014, 1-12 https://armypubs.us.army.mil/doctrine/DR_pubs/dr_a/pdf/adrp6_0.pdf.
- S. Department of Defense, “JP 3-60, Joint Targeting,” January 31, 2013, C-7 https://jdeis.js.mil/jdeis/new_pubs/jp3_60.pdf.
- Department of the Army, “Army Techniques Publication (ATP) 3-60,” May 1, 2015, 2-1 http://armypubs.army.mil/doctrine/DR_pubs/dr_a/pdf/atp3_60.pdf.
- S. Department of Defense, “Joint Publication (JP) 3-12, Cyberspace Operations,” February 5, 2013, 1-7 http://www.dtic.mil/doctrine/new_pubs/jp3_12R.pdf.
- Non-doctrinal terms utilized to illustrate the differences (time, coordination, scope) in requested cyber effects. Considering the unique nature of each cyber tool that is developed; this was an attempt to classify, in general terms, types of effects.
- Department of the Army, “ADRP 5-0, The Operations Process,” May 17, 2012, 1-7 http://armypubs.army.mil/doctrine/DR_pubs/dr_a/pdf/adrp5_0.pdf.