DESCRIPTION OF ISSUE / PROBLEM STATEMENT
1. Describing the challenge of converging CO and EW effects requires first to define each and their interaction within the Open Systems Interconnection (OSI) model. The OSI model is a standard model to describe a seven-layer network protocol stack starting at the physical layer and ending at the application layer. Joint Publication 1-02, Department of Defense Dictionary of Military and Associated Terms defines cyberspace operations as “the employment of cyberspace capabilities where the primary purpose is to achieve objectives in or through cyberspace”. JP 1-02 defines electronic warfare as “military action involving the use of electromagnetic and directed energy to control the electromagnetic spectrum or to attack the enemy”. While the definitions have little in common, CO and EW are both based on three roughly similar pillars: attack, defense, and support/operations. For cyberspace operations, the pillars are defined as Offensive Cyber Operations (OCO), Defensive Cyber Operations (DCO) and DoD Information Network (DODIN) Operations.3 These mission categories align well with the electronic warfare missions of Electronic Attack (EA), Electronic Protection (EP) and Electronic Warfare Support (ES). OCO projects power “by the application of force in and through cyberspace”, while EA involves the use of “EM energy, DE, or antiradiation weapons to attack personnel, facilities, or equipment with the intent of degrading, neutralizing, or destroying enemy combat capability.”4 The convergence of OCO and EA effects is highlighted in Figure 1 below with Computer Network Operations (CNO) being a legacy term used to describe OCO.
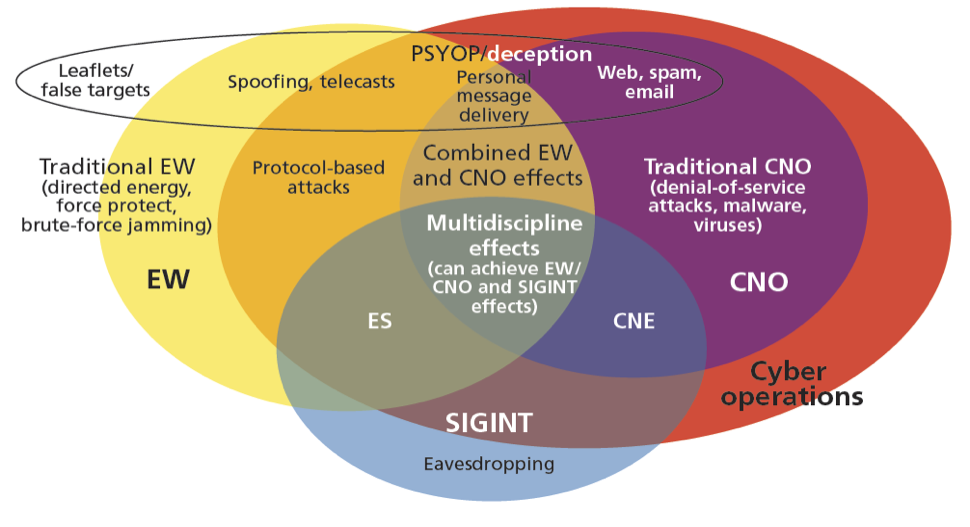
Figure 1. Functional View of Converging Areas According to CERDEC Draft (Reprinted from Porche, et al., “Redefining Information Warfare Boundaries for an Army in a Wireless World,” p.51)
DCO uses passive and active cyberspace capabilities to “protect data, networks, net-centric capabilities, and other designated systems,” with EP being “actions taken to protect personnel, facilities, and equipment from any effects of friendly or enemy use of the electromagnetic spectrum that degrade, neutralize, or destroy friendly combat capability.”5 DODIN Operations are actions taken to “design, build, configure, secure, operate, maintain, and sustain DoD communications systems and networks in a way that creates and preserves data availability, integrity, confidentiality, as well as user/entity authentication and non-repudiation”, whereas ES is “actions tasked by, or under direct control of, an operational commander to search for, intercept, identify, and locate or localize sources of intentional and unintentional radiated electromagnetic energy for the purpose of immediate threat recognition, targeting, planning, and conduct of future operations.”6
CO and EW effects are likewise overlapped within the OSI model. Both CO and EW begin at Layer 1, the physical layer. A common misconception is that EW stops at Layer 1, but the integration of Internet Protocol (IP) into a wide range of communications systems enables intelligent jamming. In intelligent jamming, knowledge of the protocol is incorporated into the jamming technique.7 Solid understanding each of these specific areas and their overlap is critical to achieving capability convergence and the resulting combined CO and EW effects.
2. In Convergence of Electronic Warfare and Computer Network Exploitation/Attacks Within the Radio Frequency Spectrum, David Rohret and Abiud Jimenez, members of the Joint Information Operations Warfare Center (JIOWC) / Vulnerability Assessment Team (VAT), describe how the integration of IP capabilities in systems using Radio Frequency (RF) for communication provides attackers the ability to exploit systems on isolated networks. Unlike current cyber and EW protection teams, which are focused on vulnerabilities within their respective areas, adversaries are focused on achieving desired effects and end state goals. This threat is heightened by oversights in software and communications system developers in recognizing vulnerabilities introduced during the integration of hardware and software. This paper covers three case studies based on actual vulnerability assessments highlighting these issues. In the first case study, an IP over radio system developed to provide high bandwidth connections from an aerial platform to users on the ground was effectively disabled through the use of intelligent jamming. The IP over radio system was protected from traditional networks attacks through the use of a proprietary secure wireless protocol, but it proved highly vulnerable to center band frequency jamming at power levels so low, the denial of service was attributed to a system error instead of jamming.8 In the second case, OCO and EW capabilities were synchronized in a simulated attack against a satellite communication (SATCOM) network. OCO was used to gain access and enumerate the SATCOM network to identify the ground station, which was them jammed forcing the target to use alternate communications methods, thus providing potential new avenues of attack with their own vulnerabilities.9 In the third case study, a coordinated CO and EW attack on a sensor network enabled the mesh network to be severely degraded, preventing data from the sensors from being received without triggering an alert from a denial of service or jamming attack.10 These examples demonstrate the power of synergistic effects created through the convergence of CO and EW. Combined effects dramatically increase the difficulty for an enemy to mount an effective response as they struggle to identify the source of the attack.
3. Our adversaries will use every tool and combination thereof to achieve decisive effects on the battlefield. Prospective near-peer adversaries, Russia and China, understand the capability of converged CO and EW effects and have long standing doctrine integrating CO and EW under the umbrella of Information Warfare (IW). Although the definition of IW and the elements of IW differ between Russia and China, both are focused on achieving combined effects.11 While Russian definition of IW varies depending on the agency involved, it is roughly defined as an integrated system of system for “establishing control over other states’ information resources … disrupting … information networks and communications systems, and developing information weapons.”12 Russian IW includes elements of “intelligence and counterintelligence gathering, disinformation, use of EW systems, debilitation of communications and scrambling of enemy data, use of psychological pressure on the enemy, and destruction of enemy computer nets and software programs.”13 The Chinese definition of IW is more vague, but generally emphasizes three pillars, psychological operations, denial and deception.14 Chinese IW includes elements of precision strike warfare to destroy enemy command and control facilities, EW to “dominate the spectrum while denying the enemy’s effective use of electronic equipment”, computer network warfare, which covers a wide spectrum of capabilities and psychological warfare and deception to influence behavior of targeted elements.15 The key takeaway is that both of these potential near-peer adversaries have integrated CO and EW capabilities to achieve combined IW effects. Given their interest and investment in asymmetric capabilities to overcome US military superiority and the DoD’s reliance on the availability of the electromagnetic spectrum for command and control, the threat of combined CO and EW operations poses a significant threat.
4. While the Air Force, Marine Corps and Navy has well established EW career fields, organizations and training programs, the Army’s Electronic Warfare branch, Career Management Field (CMF) 29 was established in 2012. The Army maintained communications electronic warfare battalions during the Cold War, but were disbanded in the 1990s, causing significant deficiencies in electronic warfare capabilities, which were grimly recognized during combat operations in Iraq and Afghanistan. With less than 1,000 officers, warrant officers and enlisted personnel, the EW career field has struggled with finding its role as combat deployments have significantly decreased. As a result, when not deployed, EW personnel are often assigned to other duties, resulting in EW is often derided as standing for “extra worker”.16 Exacerbating this problem, the Army will not field a standard electronic warfare capability, with the Multifunctional Electronic Warfare (MFEW) program not slated to reach initial operating capability until 2023.17 Currently the Army electronic warfare capabilities are focused on countering remote controlled improvised explosive devices, but programs are in place to develop an integrated EW Planning and Management Tool (EWPMT) to provide commanders spectrum situational awareness and enable enhanced synchronization of EW capabilities.18 The Army’s Cyber branch, CMF 17 is now responsible for the management of the Army’s Electronic Warfare branch, CMF 29. The organization construct has the potential to spearhead CO and EW effects convergence within the DoD.
RECOMMENDATIONS
1. The Army should serve as a proving ground for CO and EW effects convergence due to several factors that minimize the friction to achieve effects convergence. These advantages include established doctrine converging CO and EW, unity of command at the force proponent level for CO and EW career fields and combined research and development efforts in these fields. In February 2014, the Army published FM 3-38 Cyber Electromagnetic Activities. This document provides doctrinal guidance and conducting cyber electromagnetic activities (CEMA) and the procedures and tactics for commanders and their staffs for planning, synchronizing and integrating CEMA. Due to the Army’s recent creation of both the Electronic Warfare Branch (29) and Cyber Branch (17), it is in a unique position to develop the force structures, capabilities and tools for converged CO and EW operations and effects. Both branches also currently fall under the Cyber Center of Excellence, the force modernization proponent (FMP) for cyberspace operations, signal/communications networks and information services, and Electronic Warfare. Furthermore, a single organization, the Army’s Intelligence and Information Warfare Directorate (I2WD) of the Communications-Electronic Research, Development and Engineering Center (CERDEC) is responsible for research and development of both offensive cyber operations and electronic warfare. While the Army has several advantages in being a proving ground for CO and EW effects convergence, it must leverage the knowledge and capabilities of the Air Force and Navy EW communities to tap into their wealth of experience. Lessons learned and successful pilot programs from the Army’s efforts on CO and EW effects convergence can then be introduced to Air Force and Navy CO and EW communities to accelerate the introduction of new techniques and operating concepts.
2. Additionally each Service should embrace the Marine Corps approach towards integrating CO and EW effects. The Marine Corps approach for integrating CO and EW effects focuses on the creation of a Cyber Electronic Warfare Coordination Center (CEWCC). The CEWCC is placed within a Marine Air-Ground Task Force (MAGTF) to synchronize Spectrum Warfare (SW) with a “combined arms concept for the integration of cyberspace operations, electronic warfare (EW), signals intelligence (SIGINT), spectrum management operations, and technical Information operations with conventional fires and maneuver”.19 The CEWCC is a distributed organization, which will include members and liaisons from the fields of information operations, electronic warfare, cyberspace operations and spectrum management. While still in development, the Marine Corps is aggressively developing the CEWCC concept with an interim publication and ongoing proof of concept within the 13th Marine Expeditionary Unit.20 The concept of SW, which focuses on the relationships within cyberspace and the electromagnetic spectrum, provides a good framework for the integration of cyberspace operations and electronic warfare.
COUNTERARGUMENT
Convergence of CO and EW effects will reduce the ability of commanders to employ offensive EW capabilities given national level approval is required to conduct OCO.21 In contrast, employment of offensive EW, or EA capabilities typically requires approval only at the operational or tactical level. Commanders with EA assets are able to rapidly impact an adversary’s radio communications network through jamming of the links or use of directed energy weapons to destroy the transmitters. The use of OCO to produce the same effect of denying the enemy use of the radio communications network would require “careful planning, in-depth intelligence support, and interagency coordination” in addition to national level approval.22 Convergence of OCO and EA has the potential of denying commanders the use of an effective, rapidly employable capability by tying a capability that requires only tactical or operational level approval to one that requires national level approval.
Convergence of CO and EW effects will further limit the resources available for EW given the near insatiable demand for resources to develop OCO capabilities, conduct DCO and operate the DODIN. EW capabilities are employed primarily during Phase 2: Seize the Initiative of the continuum of military operations. Conversely CO are employed during all phases of the continuum of military operations, which helps account for the high level of resourcing invested in CO capabilities.
Given the Army’s nascent CO and EW capabilities and experience, it is a poor choice to serve as a proving ground for CO and EW effects convergence. Even successful CO and EW effects convergence pilot programs in the Army will be difficult to transition to the Air Force and Navy with fundamentally different requirements for the employment of employment and desired effects of CO and EW effects. Additionally, given the current budget constrained environment and heightened threat level, resources should be focused on enhancing current capabilities instead of investing in unproven concepts.
CONCLUSION
In an environment of limited budgets, EW practitioners face a difficult challenge in obtaining resources to fully leverage EW due to the intense focus on CO. While senior military leaders speak of full integration of CO and EW effects, the distinct differences between the two fields and limited experience employing CO in conjunction with EW capabilities, inhibits this integration, reducing their effectiveness. Common understanding is the first step in achieving true convergence of CO and EW effects. Until training for CO and EW reflects convergence of their effects, Officers, Warrant Officers and Non-Commissioned Officers and civilians working in CO roles have a duty for professional self-development to educate themselves on the development and employment of EW capabilities. Likewise, EW professionals have the same obligation for professional self-development on CO. Convergence begins with shared understanding, shared understanding starts with each of us.
About the author
MAJ Michael Senft is a FA24 and currently assigned to the Office Chief of Signal as the FA24 Career Program Manager. Michael has completed multiple deployments as a Network Engineer supporting Joint and Special Operations units. He holds a Master’s Degree in Computer Science from the Naval Postgraduate School, a Master’s Degree in Engineering Management from Washington State University and a Bachelor’s Degree in Mining Engineering from Virginia Tech.
ENDNOTES
- Sydney Freedberg Jr., “Wireless Hacking In Flight: Air Force Demos Cyber EC-130.” Breaking Defense. Retrieved from http://breakingdefense.com/2015/09/wireless-hacking-in-flight-air-force-demos-cyber-ec-130/, (2015).
- Ibid.
- JP 3–12 (R), Cyberspace Operations. Retrieved from http://dtic.mil/doctrine/new_pubs/jp3_12R.pdf, (2013), II-2.
- Ibid. p.II-2 and JP 3–13.1 (2014). Electronic Warfare. Retrieved from http://dtic.mil/doctrine/new_pubs/jointpub_operations.htm, I-4.
- Ibid., II-2 and Ibid., I-6.
- Ibid., II-3 and Ibid., I-6.
- David Theunte & Mithun Archarya, “Intelligent Jamming in Wireless Networks with Applications to 802.11b and Other Networks.” Proceedings of the 2006 IEEE conference on Military communication. Retrieved from http://networking.ncsu.edu/ThuenteMilcom06_FINAL.pdf, (2006), 5.
- David Rohret & Abuid Jimenez, “Convergence of Electronic Warfare and Computer Network Exploitation/Attacks Within the Radio Frequency Spectrum.” Proceedings of ICIW 2012 The 7th International Conference on Information-Warfare & Security. Retrieved from http://www.proquest.com, (2012), 246.
- Ibid., 248
- Ibid., 249
- Timothy Thomas, “The Russian View of Information War.” The Russian Armed Forces at the Dawn of the Millennium. Retrieved from http://fmso.leavenworth.army.mil/documents/Russianvuiw.htm and Yoshihara, Toshi.(2001). “Chinese Information Warfare: A Phantom Menace or Emerging Threat?” Strategic Studies Institute. Retrieved from http://www.strategicstudiesinstitute.army.mil/pubs/display.cfm?pubID=62, (2000), 15.
- Ibid.
- Ibid.
- Ibid., 5.
- Ibid., 17.
- Joe Gould, “Electronic Warfare: What US Army Can Learn From Ukraine.” Defense News. Retrieved from http://www.defensenews.com/story/defense/policy-budget/warfare/2015/08/02/us-army-ukraine-russia-electronic-warfare/30913397/, (2015).
- Ibid.
- J.R. Wilson, “Not Your Old Timer’s Electronic Warfare.” Military &Aerospace Electronics. Retrieved from http://www.militaryaerospace.com/articles/print/volume-26/issue-8/special-report/not-your-old-timer-s-electronic-warfare.html, (2015)
- Matthew Poole & Jason Schuette, “Cyber Electronic Warfare.” Marine Corps Gazette. Retrieved from https://www.mca-marines.org/gazette/2015/08/cyber-electronic-warfare, (2015).
- Ibid.
- JP 3–12 (R). (2013). Cyberspace Operations. Retrieved from http://dtic.mil/doctrine/new_pubs/jp3_12R.pdf, (2013), II-7.
- Ibid.