Overview
In the 21st century, countries rely on cyberspace infrastructure for economic activity and governance. Mobile wireless networks present one indispensable part of a diverse cyberspace landscape. Mobile networks have proven essential for crisis/emergency management. This paper explores the critical importance of mobile wireless networks in future operating environments for the US military. Although the US military trains for stability operations, its current cyber doctrine primarily focuses on securing its own military infrastructure. This mindset does not adequately address the imperatives for a host nation’s cybersecurity. To be successful in future contingencies, the US military must integrate cybersecurity into its planning for stability operations. This expanded scope of cybersecurity includes restoring reliable mobile wireless networks. Mobile wireless networks have become fundamental enablers for governance and economic growth. For future operating environments, the US military must prepare teams to rapidly secure these critical mobile wireless networks.
The high importance of mobile networks during disasters
On 29 October 2012, Hurricane Sandy struck the East Coast of the United States. With an economic devastation of nearly $100 billion, Sandy was the second-costliest hurricane in US history.[1] Notwithstanding 23 other affected states, New York City suffered the hurricane’s brunt. The storm surge flooded city streets, subways, and severed power throughout the metropolitan area.[2] Before, during, and after the disaster, residents and responders relied on mobile wireless networks to communicate critical information across devastated communities.
The 14-foot storm surge flooded Lower Manhattan and knocked out Verizon’s major network hubs.[3] Persistent power outages and downed telephone wires across the City severely disrupted telecommunications. For several days, parts of NYC went without access to landline phones, wireless connectivity, or the Internet.[4] For residents with access to mobile service, the wireless network proved unable to handle the enormous traffic volume.[5] Before Hurricane Sandy made landfall, the NYC Office of Emergency Management sent mass text messages to residents in evacuation zones.[6] After the disaster hit, the City relied on “on professional contacts, crowd-sourced data, and phone interviews” to gain situational awareness and direct recovery efforts.[7]
Restoring wireless communications was critical to the City’s relief operations. NYC relied on wireless providers like Verizon to restore critical services themselves. In the meantime, FEMA and NYC deployed “Cells on Wheels” (COWs) and “Cells on light trucks” (COLTs) to provide basic mobile network coverage to residents and responders. Across the city, officials established charging stations for residents and responders to recharge mobile devices.[8] At FEMA’s Disaster Recovery Centers, kiosks “included charging stations for phones and electronic devices.”[9] Restoring basic cellular phone service played a central role in relief efforts as residents reported emergencies and responders coordinate activities.
For residents, mobile devices provided vital conduits to emergency information. The Red Cross, the Department of Veterans Affairs, and FEMA each offered smartphone apps for download.[10] These apps delivered critical information to survivors and relief workers. During Sandy, 100,000 smartphone users downloaded the Red Cross app, which provided storm tracking and emergency shelter locations. The FEMA app was downloaded 50,000 times, which offered an application tool to formally request assistance.[11] Although the storm severely disrupted mobile phone service, FEMA considered such online tools vital for crisis management.[12]
In its after-action review, FEMA cites inadequate smartphone connectivity as hampering command and control of relief operations. [13] This complaint is not unique to Hurricane Sandy. After Typhoon Haiyan in the Philippines, residents and aid organizations struggled to regain mobile service.[14] During Haiyan relief operations, EU Humanitarian Aid commissioner Kristalina Georgieva said, “The first [priority] is to get access to remote areas as quickly as possible, and the access issue is both transportation and also restoring telecommunications.”[15] The rapid restoration of mobile networks in New York after Hurricane Sandy appears incredible when compared to the pace seen in the less wealthy communities. Some countries do not necessarily enjoy America’s robust resources alongside institutionalized public-private partnerships.
For the first time in its 30-year history, Groupe Speciale Mobile Association (GSMA) deployed a Disaster Response Coordinator to manage the high demand for mobile wireless networks.[16] GSMA is a private industry body representing over 250 telecommunications companies like AT&T, MTN, Orange, Telenor, Verizon, and Vodafone.[17] On 2 March 2015, the GSMA signed a Humanitarian Connectivity Charter.[18] The telecommunications industry believes mobile networks play a critical role during humanitarian crises. In its press release, GSMA states, “Mobile devices are often one of the first things people reach for when disaster strikes; for example, one of the first requests by those displaced on Sinjar Mountain in Iraq was a means to charge their mobile phones so that they could obtain information, to locate loved ones and to become involved in response efforts.”[19] In 2015, mobile networks have become an essential feature of crisis/emergency management.
Recent crises have demonstrated the indispensable power of mobile networks, which is one manifestation of cyberspace. During the Ebola outbreak in 2014, the Sierra Leone government used text messages to transmit public health messages.[20] Mobile data sharing proved essential in recovery efforts after the 2010 earthquakes in Haiti and Chile.[21] After the 2015 earthquake in Nepal, mobile networks enabled life-saving communication between relief workers and local citizens.[22] In response to the 2011 earthquake/tsunami disaster in Japan, local citizens depended on mobile networks to retrieve emergency response information.[23] After the 2013 Boston Marathon Bombing and the 2007 San Francisco earthquake, families desperate for information via their cellphones overwhelmed America’s mobile networks.[24]
Importantly, private service providers have proven adept in some of the most challenging environments. Since the 1990s, Zimbabwe’s EcoNet has expanded mobile services and fiber-broadband across Africa.[25] India’s mobile service provides have grown into multi-billion dollar corporations.[26] One of the world’s wealthiest individuals is Mexico’s Carlos Slim, who co-chairs the Western Hemisphere’s largest mobile network service with over 270 million subscribers.[27] In Somalia, Hormuud Telecommunications (HorTel) boasts millions of active subscribers.[28]
Nevertheless, disasters and conflict can still overwhelm countries and their flagship telecommunications companies. The International Telecommunications Union (ITU) is the UN’s specialized agency for information and communications technologies (ICTs). In addition to the UN’s 173 countries, ITU includes hundreds of non-government institutions and private companies.[29] During disaster response, the UN’s ITU sends expert teams to help host nations restore telecommunications. In the first four months of 2015, ITU personnel deployed to support relief efforts in Malawi, Mozambique, Micronesia, Nepal, and Vanatu.[30] ITU worldwide employment exemplifies the acute need for assistance in developing countries to restore mobile networks.
The high importance of mobile networks for developing countries
Economic forecasters contend, “Mobility, flexibility and networks will define the future industrial landscape.”[31] Mobile wireless networks are an essential feature of this landscape. Notably, prosperity depends upon a country’s pace of adopting advanced technologies. Since 2000, information and communications technologies (ICTs) have contributed to the economic growth around the world. Access to the Internet, mobile services, and broadband connectivity significantly boosts growth (See chart below).[32]
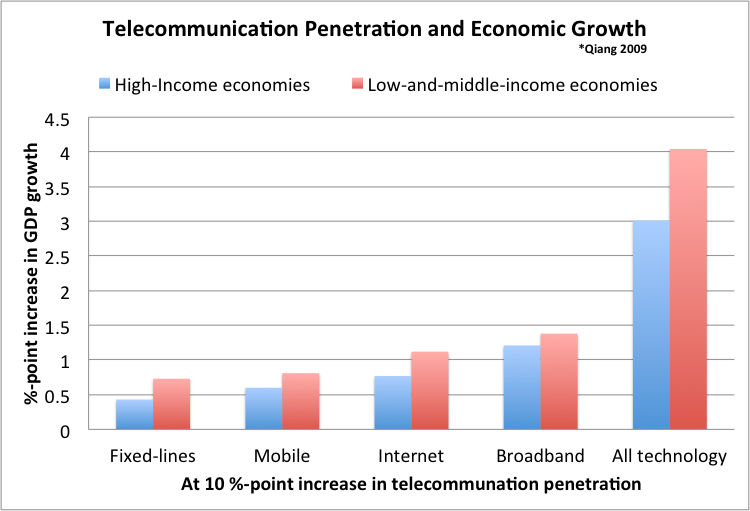
In 2013, the penetration rates in low-and-middle-income countries in mobile, Internet, and fixed-line broadband increased by 4.06, 3.01, and 0.57 percentage-points respectively.[33] A World Bank study captured in the chart above translates this expansion into a 0.76 percentage-point boost to economic growth.[34] In 2013, low-and-middle-income countries achieved 4.9% annual growth in gross domestic product (GDP).[35] Thus, rising telecommunications penetration rates may account for nearly one-sixth of their economic growth. Mobile access alone contributed to over 8% of growth. Wireless networks seemed poised to unleash latent economic forces across developing countries.[36]
Beyond economic benefits, mobile networks are spurring innovation in other areas like healthcare. Healthcare development expert Caroline Mbindyo succinctly describes the power of mobile networks:
Mobile devices can be used to provide training to all cadres of health workers across Africa, from community health workers to specialist physicians and health managers – those individuals running health facilities. They can be used to promote positive health behaviors for communities, such as the importance of hand washing. Mobile devices can track and manage health commodities to ensure that the required products are available where and when they are needed. They can be used to collect and analyze patient data, disease and condition specific data (for example TB or cervical cancer) and health facility management data. Text messages can be sent on an as-needed basis to improve health worker practices, for example, guidelines on how to provide anti-retroviral therapy to pediatric patients, or how to manage a patient with acute diarrhea.[37]
As military commanders plan for stability operations, mobile networks must be fully appreciated as an essential service. Such contingency operations require participation from governmental and non-governmental stakeholders. The challenges FEMA and New York faced after Hurricane Sandy portend future crises worldwide.
In the 2014, over 40% of the world’s population used the Internet. Developed countries still lead Internet penetration rates (78% to 34%).[38] As the pioneer of ICT, the US still leads developing economies by a factor of nearly 2 to 1. Nevertheless, emerging market economies are rapidly expanding their ICT capacity.
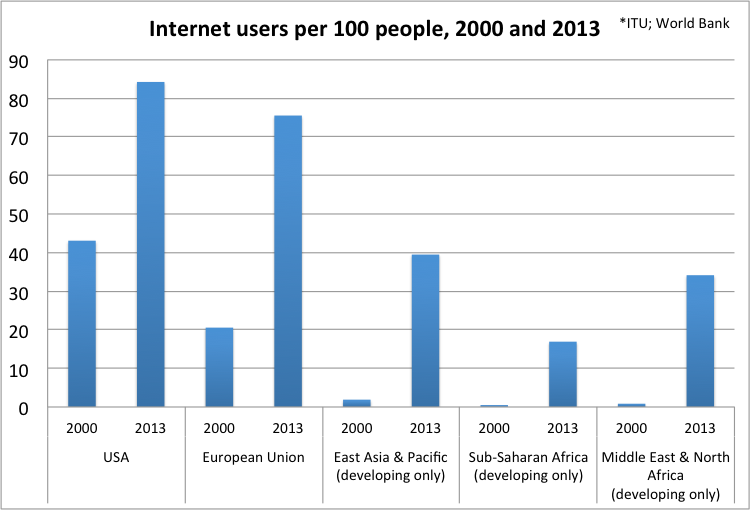
From 2000 to 2013, the Middle East and Africa experienced a 3000% expansion in Internet users. Meanwhile, Asia Pacific boasted over a 2000% expansion.
Wireless networks have enabled economic growth at the local level. Mobile phone adoption among southern India’s fishermen allowed them to research prices before docking at a fish market and significantly boost their income.[39] Since 2006, rural farmers in West Africa have used mobile phones to share real-time price information for over 80 agricultural products.[40]
Wireless networks also enable essential services in developing countries. In 2004, wireless broadband in India allowed a hospital with highly specialized eye doctors to connect with rural clinics and provide screenings for thousands of previously neglected patients. As a direct result of the virtual screenings, 85% of men and 58% of women that lost their jobs due to treatable sight impairment regained employment. By 2006, the pilot project expanded to 50 clinics with a throughput of 500,000 patients per year.[41]
Since developing countries do not possess decades of legacy systems requiring a overhaul, they can rapidly adopt newer ICTs.[42] Mobile broadband (2G or greater) continues to expand around the world.
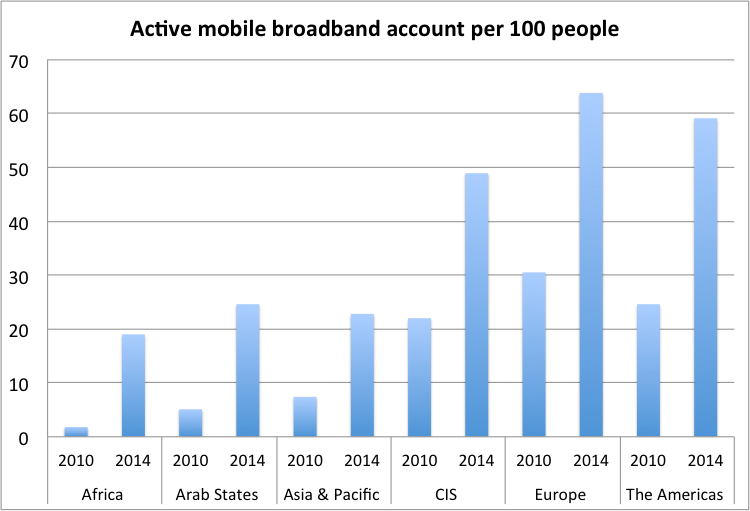
Since 2010, Africa has surged nearly 1000% in just four years. At these rates, developing countries will converge on the Europe and the US.
Positive ICT growth in developing economies also forebodes increased cyberthreats. Conflict zones already suffer elevated levels of human trafficking, child exploitation,[43] illicit drug trade, and organized crime.[44] In the future, cyberattacks will inevitably join these nefarious actors and exploit conflicts for economic gain.
The cybersecurity paradox facing developing countries
In a 2014 report, Microsoft researchers described a “cybersecurity paradox” facing developing countries. As countries become more dependent on advanced ICTs, “new threats to digital infrastructures” emerge and undermine their success.[45] Microsoft researchers found developing countries with low-levels of telecommunications penetration face the highest malware infection rates. Moreover, as these countries improve their access, infection rates actually increases.[46] Thus, the poorest countries with the shallowest ICT levels face an endemic cybersecurity threat to everyday mobile users.
In 2011, the DHS US Computer Emergency Response Team (US-CERT) warned “mobile phones are becoming more and more valuable as targets for attack.”[47] Similarly, cybersecurity professionals consider mobile devices the greatest vulnerability in cybersecurity schemes.[48] Exacerbating this vulnerability is the bring-your-own-device (BYOD) trend. BYOD companies rely on employees to use personnel computers, tablets, and smartphones to conduct business. By 2016, two-thirds of companies in North America and Europe expect to adopt this trend.[49] The global BYOD trend exposes companies to intellectual property theft and other industrial espionage.[50] This trend will indelibly shape the future operating environment for the US Army’s cybersecurity professionals.
Cyberthreats to individuals continues to be worrisome. Between August 2013 and March 2014, attacks per month on a representative sample of mobile devices rose from 69,000 to 644,000.[51] Nearly 60% of these infections were capable of stealing money from mobile banking accounts. Moreover, 57% of Trojan infections were spread via SMS/text message.[52] In 2015, investigators discovered Chinese cybercriminals using faux-mobile banking applications to fool users into entering their credentials, which allowed hackers to steal millions of dollars over a two-year period.[53]
These threats to mobile banking should concern military commanders preparing for stability operations. Mobile banking is an essential service for individuals in the developing world. In Afghanistan, police are paid via text message.[54] Pakistan’s largest financial institution is a Norwegian mobile phone operator, Telenor.[55] Kenya’s M-PESA is a popular mobile payment system rapidly expanding in emerging markets.[56]
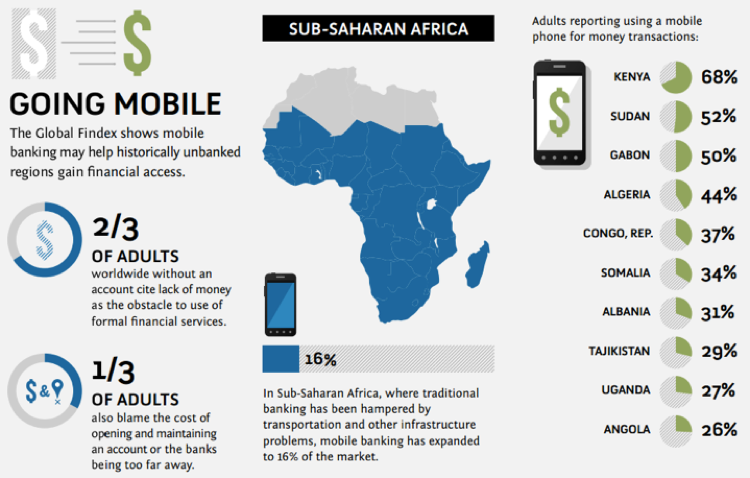
Source: World Bank Global Findex, 2012[57]
As of April 2015, 38% of the world’s population still lives without access to bank accounts.[58] Mobile banking promises to be the primary pathway to serve these communities. Over the next ten years, residents in future conflict zones will grow dependent on mobile networks for daily commerce.
In a 2007 report, ITU emphasized, “Organizations and countries need to focus on innovation capacities and rapid adaptability, backed up by a powerful and secure information system, if they wish to survive and assert themselves as long-term players in the new competitive environment.”[59] ICTs are a necessary component of prosperity, and they have been a hallmark of the world’s most successful economies.[60] Extensive World Bank studies have found “expanding access to advanced information and communication technology (ICT) services will be a key factor in sub-Saharan Africa’s economic and social development.”[61] As countries increase bandwidth capacity, the long-run costs substantially decrease, creating a virtuous cycle.[62] Lower costs spur even more broadband penetration.[63] Yet, the cybersecurity paradox demonstrates technological progress invites threats.
Conflict zones further attract threats to mobile networks. When Russia seized the Crimea, it blocked mobile phone operators in Ukraine.[64] During Kyrgyzstan’s 2005 parliamentary elections, opposition parties and independent news agencies experienced persistent disruption to their online activities. Hackers shut down opposition websites and flooded journalists’ inboxes with nefarious emails. During Belarus’s 2006 Presidential elections, these same tactics reemerged to disrupt activists seeking to unseat the incumbent president.[65] Estonia (2007) and Georgia (2008) endured persistent Russian cyberattacks against their country’s information systems.[66]
In 2013, a Ukrainian ATM began spontaneously dispensing cash to lucky pedestrians. Subsequent cyber forensics investigation revealed a $1 billion hack of over 100 banks around the world.[67] In April 2014, pro-Russian saboteurs hacked the mobile phones of Ukrainian lawmakers, severed fiber optic cables, and shutdown multiple government web sites.[68] During Ukraine’s May 2014 Presidential election, pro-Russian hackers penetrated the electronic voting system and successfully installed malicious code capable of deleting whole swaths of vote-tallies.[69]
Before 2014, Ukrainian cyberspace doctrine remained “unclear.”[70] Ukraine’s inadequate cyber policy fostered an environment US Senator Mark Kirk described as “a known hub for cybercrime.”[71] During the conflict with Russia, Ukrainians proved ill-prepared to defend their systems against emerging cyber threats.[72] In February 2015, Kiev announced a new cybersecurity strategy, which envisions “the establishment of a ‘national registry of crucial objects of national IT infrastructure’, with the aim of ensuring their protection.”[73] Ultimately, cybersecurity includes a reliable mobile network to connect the diverse information systems that underpin 21st century economies. For stability operations, telecommunications networks should be considered an essential service. If the IT systems of a government are persistently disrupted, its ability to govern is severely hampered.
Conclusion: the Army must broaden its operating concept within the cyber domain
Current military cyberspace doctrine emphasizes securing the military’s own information systems to ensure freedom of maneuver.[74] Yet, stability operations require military commanders to consider civilian infrastructure while protecting their military systems. Cyberspace infrastructure now underpins the basic functions of 21st century governments. As stability operations seek to secure a host nation, military commanders must consider non-military cyberspace imperatives. In 2014, Senators Mark Warner and Mark Kirk proposed the United States “establish a capacity-building program with Ukraine by sending FBI agents to aid Ukrainian investigations, and improve communication networks to expedite and improve law enforcement cooperation.”[75] In the future, a host nation will rely on reliable mobile wireless networks to communicate, operate critical infrastructure, and enable commerce. During crisis, the demand for function mobile wireless networks will prove even more acute.
On 2 November 1863, Colonel Anson Stager reported, “General orders are given—armies are moved—battles are planned and fought, and victories won with the assistance of this simple, yet powerful aid-de-camp, the Military Telegraph… telegraphs are the great arteries which warm the soul and keep alive the body of our grand Union army.”[76] For decades, the US military has worked to protect information systems.[77] In a 1964 publication for the US Air Force, RAND Corporation devoted an entire paper to the problem of securing information systems “because of its underlying importance both to the system and in the large, and due to a relative underdevelopment of the subject in general.”[78] In October 2014, the Joint Staff released the declassified version of its cyberspace operations doctrine, Joint Publication (JP) 3-12 Cyberspace Operations. The Joint Staff emphasizes integration of cyberspace operations with assorted organizations to perform foreign humanitarian assistance, peace operations, and other stability operations.[79] Yet, military doctrine remains focused on protecting military information systems. Nevertheless, stability operations also focus on non-military imperatives like food supply, water treatment, and electric power generation. Now, this mindset must extend to cyberspace infrastructure.
21st century economies depend on cyberspace infrastructure for economic growth and essential services. Likewise, governments rely on cyberspace to administer the physical world, such as their power grids and water treatment facilities. Future US stability operations require an integrated cybersecurity line of effort alongside its five more familiar ones from years in Iraq and Afghanistan.[80]
| Primary Army Stability Tasks + 1 |
*ADP 3-07 Stability Operations |
| Establish civil security |
| Establish civil control |
| Restore essential services |
| Support to governance |
| Support to economic and infrastructure development |
| + Secure cyberspace infrastructure ->Restore and secure mobile networks |
The simultaneity across all stability tasks requires cybersecurity to have its own line of effort. Specifically, a host nation requires mobile wireless networks to provide essential services while conducting sufficient crisis management response for civil security, civil control, and governance.
Ultimately, the military must ensure its cyber capabilities to maneuver on the battlefield. Therefore, the military must retain a robust cyber defense for its military cyber infrastructure. Yet, for stability operations, cybersecurity extends beyond these systems to civilian networks. Going forward, the Army must prepare for the cyberspace of stability operations. In addition to numerous daunting tasks,[81] cyber mission forces will support host nation achieve basic cybersecurity. The Army must be ready to rapidly restore reliable mobile networks that increasingly underpin societies around the world.
Endnotes
[1]. “Hurricane Sandy event overview,” NOAA’s National Weather Service (2012). http://www.erh.noaa.gov/mhx/EventReviews/20121029/20121029.php.
[2]. Ibid.
[3]. New York City Hurricane Sandy After Action Report and Recommendations, prepared for Mayor Michael Bloomberg, Deputy Mayor Linda I. Gibbs and Deputy Mayor Caswell F. Holloway (May 2013), 24.
[4]. Ibid.
[5]. Ibid.
[6]. Ibid., 6.
[7]. Ibid., 21.
[8]. Ibid., 37.
[9]. Hurricane Sandy FEMA After-Action Report, Federal Emergency Management Agency (1 July 2013), 21.
[10]. Ibid., 27.
[11]. Ibid.
[12]. Ibid.
[13]. Ibid., 37.
[14]. “The CDAC Network: Typhoon Haiyan Learning Review,” Communicating with Disaster Affected Communities (CDAC) Network (November 2014), 20.
[15]. “Typhoon Haiyan: Philippines destruction ‘absolute bedlam’” BBC News. 11 October 2013.
[16]. Ibid., 37.
[17]. “Brief History of GSM & the GSMA,” Groupe Speciale Mobile Association, 2015, http://www.gsma.com/aboutus/.
[18]. “GSMA Launches Humanitarian Connectivity Charter,” Groupe Speciale Mobile Association Press Release (2 March 2015), http://www.gsma.com/newsroom/press-release/gsma-launches-humanitarian-connectivity-charter/.
[19]. Ibid.
[20]. “Which doctor?: Ebola in Sierra Leone,” Economist (19 June 2014).
[21]. “A web of support: Online crisis management.” Economist (14 July 2014).
[22]. John Ribeiro, “Internet becomes a lifeline in Nepal after earthquake,” Computer World (25 April 2015).
[23]. “The information equation: Dealing with Japan’s disaster,” Economist (24 April 2011).
[24]. Neal Ungerleider, “Why Your Phone Doesn’t Work During Disasters,” Fast Company, 17 April 2013.
[25]. “Many rivers to cross,” Economist (5 July 2014).
[26].“Net neutrality in India,” Economist (25 April 2015); “Mobile telecoms in India,” Economist (21 May 2015).
[27]. Patricia Laya, “Carlos Slim to Dismantle Mexican Empire,” Bloomberg, 9 July 2014.
[28]. “Market Overview – Somalia – Mobile Growth Forecast,” BMI Research (Oct 2014), http://www.telecomsinsight.com/market-overview-somalia-mobile-growth-forecast-oct-2014 [accessed 1 June 2015].
[29]. “ITU Disaster Response,” ITU (April 2015) http://www.itu.int/en/ITU-D/Emergency-Telecommunications/Pages/Response.aspx [accessed 1 May 2015].
[30]. Ibid.
[31]. “Ten thoughts for the future: Friends and forecasters,” Economist (17 Dec 2013).
[32]. Christine Zhen-Wei Qiang, “Mobile Telephony: A Transformational Tool for Growth and Development.” Private Sector Development, No. 4 (November 2009).
[33]. ‘’ICT Statistics,” ITU (2015), http://www.itu.int/en/ITU-D/Statistics/Pages/default.aspx
[34]. Christine Zhen-Wei Qiang, “Mobile Telephony: A Transformational Tool for Growth and Development.” Private Sector Development, No. 4 (November 2009).
[35]. “Global Economic Prospects,” World Bank (2015). http://www.worldbank.org/en/publication/global-economic-prospects/regional-outlooks/ssa
[36]. “The role of Wi-Fi in developing nations,” Wireless Broadband Alliance (24 April 2014), http://www.wballiance.com/industryinsights/the-role-of-wi-fi-in-developing-nations/.
[37]. Caroline Mbindyo, interviewed by Tom Watson, “Going Mobile In Sub-Saharan Africa To Save Lives – And Change The Future,” Forbes (11 February 2015).
[38]. Ibid.
[39]. Robert Jensen, “The Digital Provide: Information (Technology), Market Performance and Welfare in the South Indian Fisheries Sector,” The Quarterly Journal of Economics 122(3): 879–924.
[40]. Mohsen Khalil, Philippe Dongier and Christine Zhen-Wei Qiang, “Overview,” in Information and Communications for Development 2009: Extending Reach and Increasing Impact (Washington DC: World Bank, 2009), 4.
[41]. Christine Zhen-Wei Qiang and Carlo M. Rossotto, “Economic Impacts of Broadband,” in Information and Communications for Development 2009: Extending Reach and Increasing Impact (Washington DC: World Bank, 2009), 42.
[42]. David A. Cieslikowski, Naomi J. Halewood, Kaoru Kimura and Christine Zhen-Wei Qiang, “Key Trends in ICT Development,” in Information and Communications for Development 2009: Extending Reach and Increasing Impact (Washington DC: World Bank, 2009), 130.
[43]. Human Trafficking: A Brief Overview,” Social Development Notes Conflict, Crime and Violence, No. 122 (December 2009).
[44]. “UNODC and United Nations peacekeeping forces team up to combat drugs and crime in conflict zones,” United Nations Office on Drugs and Crime UNODC (2 March 2011).
[45]. David Burt, Paul Nicholas and Kevin Sullivan, “The Cybersecurity Risk Paradox: Impact of Social, Economic, and Technological Factors on Rates of Malware,” Microsoft Intelligence Report Special Edition (2014), 2
[46]. Ibid. 8.
[47]. Paul Ruggiero and Jon Foote, “Cyber Threats to Mobile Phones,” Report for US Computer Emergency Response Team (US-CERT), prepared by Carnegie Mellon University, 2011.
[48]. “2014 Cyberthreat Defense Report: North America & Europe,” Cyber Edge Group (2014), 5
[49]. Ibid., 28.
[50]. Wenke Lee and Bo Rotoloni, eds, “Emerging Cyber Threats Report 2014,” Georgia Tech Cyber Security Summit 2013 (2014), 28.
[51]. “Mobile Cyber Threats,” Kaspersky Lab and INTERPOL Joint Report. October 2014, 13.
[52]. Ibid., 13.
[53]. Pierluigi Paganini, “Yanbian Gang steals millions from mobile banking customers of South Korea,” Security Affairs (18 February 2015), http://securityaffairs.co/wordpress/33709/cyber-crime/yanbian-gang-mobile-banking.html.
[54]. ”Global trends in mobile banking.” IGATE Corporation White Paper (2014), 3.
[55]. Ibid.
[56]. Ibid.
[57]. “Who are the unbanked?” World Bank (2012), http://siteresources.worldbank.org/EXTGLOBALFIN/Resources/8519638-1332259343991/world_bank3_Poster.pdf [accessed 25 October 2015].
[58]. Asli Demirguc-Kunt, Leora Klapper, Dorothe Singer and Peter Van Oudheusden, “The Global Findex Database 2014 Measuring Financial Inclusion around the World,” World Bank Group (April 2015).
[59]. Cybersecurity guide for Developing Countries (Geneva: Telecommunication Development Bureau, 2007), 7
[60]. A. Colecchia and P. Schreyer, “ICT Investment and Economic Growth in the 1990s: Is the United States a Unique Case? A Comparative Study of Nine OECD Countries,”OECD Science, Technology and Industry Working Papers (July 2001), 4.
[61]. Mark D. J. Williams, “Advancing the Development of Backbone Networks in Sub-Saharan Africa,” in Information and Communications for Development 2009: Extending Reach and Increasing Impact (Washington DC: World Bank, 2009), 4.
[62]. Ibid.
[63]. ICT Facts and Figures (Geneva: International Telecommunication Union, February 2013).
[64]. Shane Harris, “Hack Attack: Russia’s first targets in Ukraine: its cell phones and Internet lines.” Foreign Policy (3 March 2014). http://foreignpolicy.com/2014/03/03/hack-attack/ [accessed 1 April 2015].
[65]. Ronald J. Deibert, Black Code: Surveillance, Privacy, and the Dark Side of the Internet (Toronto: McClelland & Stewart, 2013), 156.
[66]. Michael N. Schmitt, ed., Tallinn Manual on the International Law Applicable to Cyber Warfare (New York: Cambridge University Press, 2013), 69.
[67]. “Hackers Steal Up to $1 Billion From Banks, Security Co. Says,” New York Times, 5 February 2013.
[68]. Tim Maurer, “Efforts made to improve global cyber-security,” Jane’s Intelligence Review (23 February 2015).
[69]. Mark Clayton, “Ukraine election narrowly avoided ‘wanton destruction’ from hackers,” Christian Science Monitor, 17 June 2014, http://www.csmonitor.com/World/Passcode/2014/0617/Ukraine-election-narrowly-avoided-wanton-destruction-from-hackers-video [accessed 25 February 2015].
[70]. James A. Lewis, Katrina Timlin, “Cybersecurity and Cyberwarfare (2011): Preliminary Assessment of National Doctrine and Organization,” Center for Strategic and International Studies (2011), 19. http://unidir.org/files/publications/pdfs/cybersecurity-and-cyberwarfare-preliminary-assessment-of-national-doctrine-and-organization-380.pdf [accessed 25 February 2015].
[71]. “Sens. Warner, Kirk to Introduce Cybersecurity Amendment to Ukrainian Aid Bill on Monday,” Mark Warner (23 March 2014) http://www.warner.senate.gov/public/index.cfm/2014/3/sens-warner-kirk-to-introduce-cybersecurity-amendment-to-ukrainian-aid-bill-on-monday [accessed 12 November 2015].
[72]. Jason Healey, “Russia vs. Ukraine: The Cyber Front Unfolds,” New Atlanticist (The Atlantic Council’s Public Policy Blog), 2 April 2014, http://www.atlanticcouncil.org/blogs/new-atlanticist/russia-vs-ukraine-the-cyber-front-unfolds [accessed 25 February 2015].
[73]. Eugene Gerden, “Ukrainian government to counter cyber-attacks,” SC Magazine: For IT Security Professionals (February 13, 2015) http://www.scmagazineuk.com/ukrainian-government-to-counter-cyber-attacks/article/397970/ [accessed 25 February 2015]
[74]. JP 3-12 (R), vi.
[75]. “Sens. Warner, Kirk to Introduce Cybersecurity Amendment to Ukrainian Aid Bill on Monday,” Mark Warner (23 March 2014).
[76]. William Rattle Plum, The military telegraph during the Civil War in the United States : with an exposition of ancient and modern means of communication, and of the federal and Confederate cipher systems (Chicago : Jansen, McClurg & Company, 1882), 366.
[77]. David E. Pearson, The World Wide Military Command and Control System: Evolution and Effectiveness (Maxwell Air Force Base, Alabama: Air University Press, 2000), 19.
[78]. Paul Baran, On Distributed Communications:: IX. Security, Secrecy, and Tamper-Free Considerations (Santa Monica, CA: RAND Corporation, 1964), 1.
[79]. Joint Publication 3-12(R), Cyberspace Operations, 5 February 2013, IV-14.
[80]. ADP 3-07, 11.
[81]. Todd Arnold, Rob Harrison and Gregory Conti, “Towards A Career Path in Cyberspace Operations for Army Officers,” Small Wars Journal (18 August 2014).